syscall_rule_checker Class Reference
syscall rule: More...
#include <sec_analyzer.h>
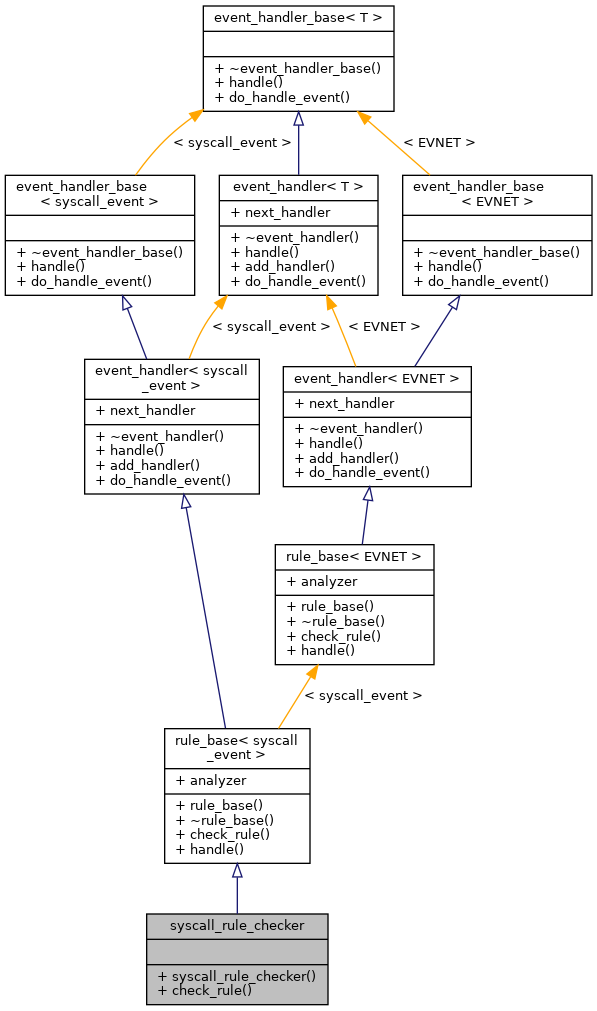
Inheritance diagram for syscall_rule_checker:
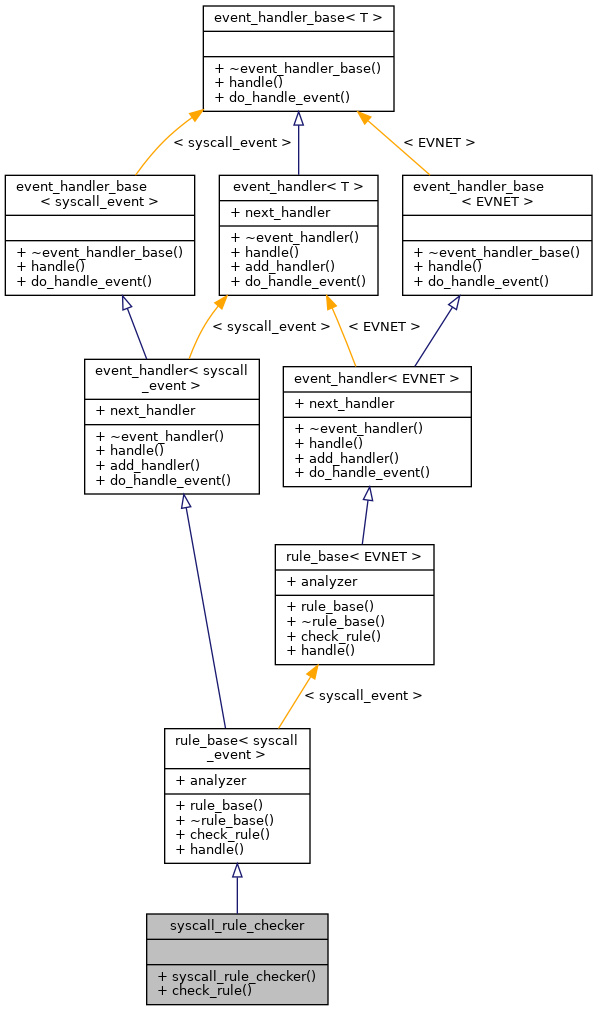
Collaboration diagram for syscall_rule_checker:
Public Member Functions | |
| syscall_rule_checker (std::shared_ptr< sec_analyzer > analyzer_ptr) | |
| int | check_rule (const tracker_event< syscall_event > &e, rule_message &msg) |
 Public Member Functions inherited from rule_base< syscall_event > Public Member Functions inherited from rule_base< syscall_event > | |
| rule_base (std::shared_ptr< sec_analyzer > analyzer_ptr) | |
| virtual | ~rule_base ()=default |
| void | handle (tracker_event< syscall_event > &e) |
| implement this function to handle the event More... | |
 Public Member Functions inherited from event_handler< syscall_event > Public Member Functions inherited from event_handler< syscall_event > | |
| virtual | ~event_handler ()=default |
| std::shared_ptr< event_handler< syscall_event > > | add_handler (std::shared_ptr< event_handler< syscall_event >> handler) |
| add a next handler after this handler More... | |
| void | do_handle_event (tracker_event< syscall_event > &e) |
 Public Member Functions inherited from event_handler_base< syscall_event > Public Member Functions inherited from event_handler_base< syscall_event > | |
| virtual | ~event_handler_base ()=default |
Additional Inherited Members | |
 Public Attributes inherited from rule_base< syscall_event > Public Attributes inherited from rule_base< syscall_event > | |
| std::shared_ptr< sec_analyzer > | analyzer |
 Public Attributes inherited from event_handler< syscall_event > Public Attributes inherited from event_handler< syscall_event > | |
| std::shared_ptr< event_handler_base< syscall_event > > | next_handler |
Detailed Description
syscall rule:
for example, a process is using a syscall
Constructor & Destructor Documentation
◆ syscall_rule_checker()
|
inline |
Member Function Documentation
◆ check_rule()
|
virtual |
Implements rule_base< syscall_event >.
The documentation for this class was generated from the following files:
- include/eunomia/sec_analyzer.h
- src/sec_analyzer.cpp
